With identity now at the forefront of cloud security, here are some of the best cloud IAM practices to follow.
As organizations continue to evolve, many are looking at multi-cloud as the answer for consuming cloud services across different cloud providers’ technologies. The idea is to decrease vendor lock-in risks and benefit from using various pricing models. However, this model adds complexity to cloud identity and access management (IAM).
The more an organization uses cloud services, the more various identities are associated with these cloud service provider environments. This becomes a problem for monitoring, tracking, and controlling cloud accounts, including accessing cloud resources. Since cloud resource access is primarily determined by identity, it’s the new perimeter and parameter for assessing cloud security today. In fact, even the Cloud Security Alliance’s “Top Threats to Cloud Computing – Pandemic Eleven” report lists identity management as the top threat to cloud security.
With identity now at the forefront of cloud security, here are some of the best cloud IAM practices to follow.

Define, enforce, and monitor roles, duties, and privileges in the cloud
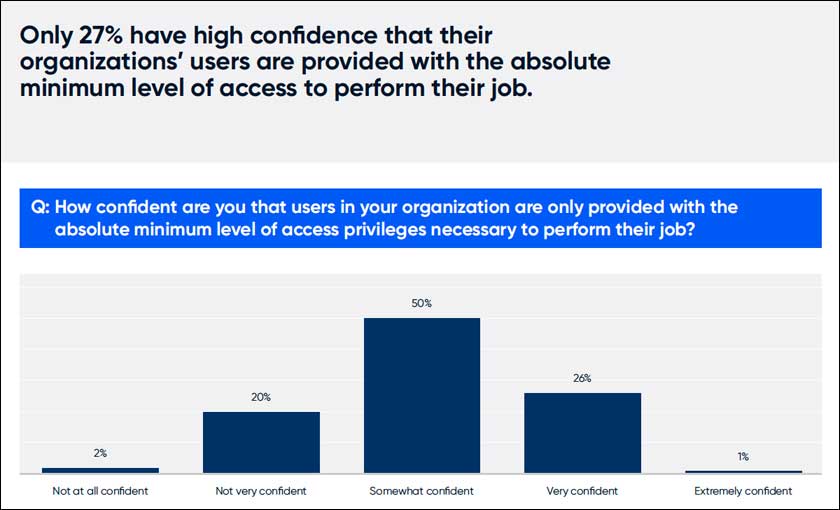
With the growth of DevOps, it’s easy for privileges to converge and the number of identities and roles to spiral out of control. In fact, even a March 2024 Cybersecurity Buyer Intelligence Report (CBIR) report states that users have more access than they need. So, organizations must quickly identify cloud resources with unintended cross-account or public access that could bring in new risks. They should train and assist security teams in discovering how these privileges are created and used going forward. Moreover, they should assess resource policies and develop internal standards for account creation practices governing how different teams integrate identities and privilege models into cloud deployments.
Businesses should also consider using integrated identity scanning and analysis tools, that could constantly monitor for any updated/new policies and analyze any permissions that resources have been granted in their respective cloud environments. The idea is to incorporate the principle of least privilege so as to ensure that every cloud account can only access what the user needs to do their job.
For instance, the IAM Access Analyzer from Amazon Web Services (AWS) discovers all resources and identities accessible from outside AWS accounts. Plus, it validates cross-account and public access before deploying permission changes.
Logging privileged access
An important task that organizations need to do is log all privileged access, including DevOps, admins, etc., to avoid the occurrence of any illicit activity. Furthermore, they need to coordinate and distil into meaningful activities in complex and busy environments. But that’s not all. Implementing Multi-Factor Authentication (MFA) for privileged admin accounts is one of the simplest and best IAM practices. This extra step makes it more difficult for hackers to gain access to these accounts, rendering traditional credential attacks ineffective.
Automating de-provisioning
As important as it is to log privileged accounts and access, another critical factor that remains a classic IAM challenge in de-provisioning, both in the cloud and on-premises. Organizations should immediately de-provision accounts as soon as the user leaves the company, either doing away with it or rendering it inactive. Automating de-provisioning processes not only improves multi-cloud security but also reduces admin workloads.

Centralizing cloud IAM accounts
With growing DevOps automated pipeline activities, it’s critical for organizations to centralize and control internal DevOps privileges, including certificates, passwords, and keys, as well as cloud IAM accounts and access keys. This could require using an encrypted secrets vault.
Another critical way to improve security is to centralize authorization and authentication for end-user accounts through a single sign-on (SSO) portal, thus creating a secure “front door” to all services and apps and protecting it.
While most organizations employ some or the other cloud management practices and models, another model is slowly emerging as a solution for this multi-cloud IAM problem: Identity as a Service (IDaaS). It’s a departure from traditional on-premises IAM systems and floats the idea of a “Unified Identity” by centralizing the management of security policies, user identities, and access privileges. Thus, it offers a more efficient, scalable, and flexible way to handle IAM. Not only does it have Single Sign-On capabilities, but it also includes MFA, centralized identity management, auditing, and compliance.
While the realm of cloud IAM continues to evolve, it also presents newer challenges and threats. Not only is it one of the most critical security control areas, but it is also not easy to manage at scale. Using these best practices, organizations should double down on cloud IAM controls to ensure that identity/ access controls are effective and secure across cloud environments.
In case you missed:
- Top cloud migration myths
- All About Attack Surface Management
- Enterprise Network Transformation: Benefits and Challenges
- Keeping Your Tech Tidy: Tips For Data Backup And Safety
- Colocation Data Centres: An Overview
- Everything you need to know about DaaS (Desktop as a Service)
- Edera: An All-Women Startup Revolutionising Cloud And AI Infrastructure Security
- Cryptography in Network Security – Concepts and Practices
- Re-examining Cybersecurity through Blockchain
- Why You Should Use Password Managers in 2025










