In the first part of this trilogy, we talked about 10 most common ways India’s cybercriminals target us while here Satyen K. Bordoloi expands the crimeverse with 15 more ways in which they can cheat you and in the next part, how you can arm yourself against them.
Last September, when Assam Police Crime Branch received a tip-off about a fake call centre in Guwahati, they believed it to be a routine job. But what Guwahati Police ended up unearthing, was a multi-crore scam that had eight illegal call centres to scam both Indians and foreigners in the guise of offering technical support. These ‘call centres’ were running for two years with employees from all over India. Three masterminds were arrested and nearly 200 ’employees’ were detained.
In the previous part, we highlighted the 10 most common ways cybercriminals target us as highlighted by the Indian Cybercrime Coordination Centre (I4C). In this part, we will expand the crimeverse to tell you of 15 more ways in which you can fall prey to scammers and lose your precious money and peace of mind.

FAKE TECH SUPPORT SCAM:
If one coordinated raid in far-off Guwahati can unearth 8 call centres generating crores every month, you can imagine the extent this scam is thriving across India. Indeed, in the last few years, police across the nation have made numerous arrests where cybercriminals ran fake tech support. The way it works is simple: a pop-up when you visit some website would lure you to them, or they’d contact directly claiming to be from a well-known company or organization like a bank, a tech support company, government agency etc. They claim your bank account has been compromised, your computer has a virus, or your social media account has been hacked etc. They don’t ask for money but will ask you to install remote desktop software on your ‘infected’ device to remedy it. Later, they’d steal your money by getting access to your bank accounts, passwords etc. by planting malware.

ONLINE QUIZZES AND SURVEYS:
Quizzes or surveys on sites may seem harmless. But these can be used to collect your personal information, which can lead to identity theft and social engineering scams where scammers impersonate people close to you to steal money or data. Be careful about the information you give out in such surveys, and ideally fill them up only if they are from absolutely reliable sources.
PUBLIC Wi-Fi TRAPS:
Free Wi-Fi at public places like train, bus or plane stations is always enticing. But these can be traps deliberately set up by cybercriminals. Once you use their network, anything you send to them could be intercepted by them. In trying to save a few rupees, you could lose much more in such unsecured public Wi-Fi networks
PIGGYBACKING AND SHOULDER SURFING:
A few weeks ago, Wall Street Journal did a brilliant series including a podcast about how criminals steal phones at public places. When you use a password to open your phone in public, someone around might be watching you enter it. If they steal your phone left on the bar or table later, they can open it with the password they saw over your shoulders. The WSJ series highlighted how by doing this they can not only steal money, but lock you out of all your data, including photos and wipe them clean, in essence erasing your memories, and hack your social media and other accounts as well.
RANSOMWARE:
Last year AIIMS, Delhi was locked out of their own computer systems after ransomware debilitated them. The attackers asked for money to restore it. Though, usually, ransomware peddlers target big companies or institutions, individuals aren’t safe either and as we highlighted in a previous article on Sify, we must be wary.
PYRAMID SCHEMES / INVESTMENT SCAMS / CRYPTO SCAMS:
Yes, the old-world pyramid schemes of the physical world, have a digital avatar. The scam is often simple: ‘invest’ money for a set period via an app that promises to double it – sometimes it is via cryptocurrency, inspire others to do the same and get rich. A relative in Assam lost over a lakh to this scam where they doubled their small initial investment within months, but once they and others they inspired had invested more, the app and company disappeared. These scammers sometimes use the mumbo-jumbo of cryptocurrency. Beware of such fake investments, pump-and-dump, pyramid and/or crypto scams, Ponzi schemes, and fraudulent exchanges that promise you a doubling of your money in a short time.

DATING SCAMS – LOCAL AND INTERNATIONAL:
This has many variants. Women lure rich men on dating or marriage portals, build a relationship – sometimes sexual – to gain trust and later blackmail people. The male version works on matrimonial sites where a man pretends to be a rich guy or a high-profile government servant but disappears before or after marriage after extracting money from the woman or her family. The international version is when an NRI pretends to have a high-paying job in a foreign country, marries and takes dowry and either never takes the girl abroad, or takes her and either dumps her or uses her like a slave. A smaller version of this scam is when a woman calls a man matched on a dating app for a date in a pre-fixed restaurant and has dinner and drinks that should have cost a few thousand, but cost him ten or fifteen times more.
FAKE JOB OFFERS:
Another friend lost nearly a lakh to scammers who contacted him via legitimate-looking emails to get him a job in Canada. The job wasn’t there, and the men disappeared once they had his money. Luring victims with appealing job offers whether in the same nation or abroad to steal personal information or money has become a lucrative method used by cybercriminals to exploit the vulnerabilities of people.

STEALING CREDIT/DEBIT CARD DATA:
The guy at the counter gave me the POS card terminal for me to enter my password for payment. I did while hiding the keypad. He took the terminal, looked at it and said sorry, I had forgotten to enter the amount. What that person had done, was very smartly figure out how to know my four-digit debit card passcode. That, along with skimming my card which he could have done since I handed him the card inside his cabin and wasn’t paying enough attention, he now had access to my card data which he could have used for anything, except, I changed my pin once again because I saw this. This was a sophisticated operation, but usually, it is done using a compromised payment terminal or via phishing.
‘BOSS SCAM’ OR BUSINESS EMAIL COMPROMISE (BEC):
The COVID pandemic made work from home a necessity. As we worked away from one another, the BEC or ‘Boss Scam’, emerged. This is a type of cyber-attack where fraudsters impersonate top executives of a company, and feign a work emergency to pressure an employee into acting quickly to either transfer money or share data that can be used to compromise later. You can read an example of this in the beginning of the next part of this series.
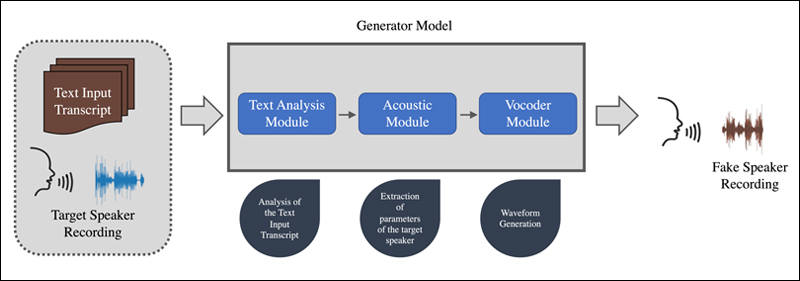
VOICE AND VIDEO DEEPFAKES:
You get a call from a lawyer saying your son, daughter or grandchild is in trouble as they have been arrested. They give the phone to this relative in trouble and sure enough, you hear their panicked voice and know it is them, so you do what the ‘lawyer’ tells you and transfer money. It is only later, that you realise that you have been scammed as the said relative in question had always been safe. These are new kinds of scams where using just a few second sample of someone’s sound, AI can be used to replicate them and fool people in this way.
MOBILE APP THREATS:
The reason why both Apple with their App Store and Google’s Play Store are so particular that you download apps only from their stores, is because they check the apps posted there. Yet, occasionally some do slip through and these malicious apps or adware on mobile devices can steal data, track location, or spy on your activities. Downloading and using apps from outside these official app stores is extremely risky.
(Image Created on Bing.com)
INTERNET OF THINGS (IoT) EXPLOITATION:
You can switch on the AC of your home from your mobile device while you’re still on the way, or change the colour of your electric bulb. Life has become easy and fun thanks to IoT devices connected to the network. However, these devices can become another way by which hackers can gain access to either your personal information or disrupt networks.
ZERO-DAY ATTACKS:
Along with Phishing, this is one of the oldest ways of hurting a digital user. Every program or system we install on our digital devices could have previously unknown vulnerabilities in their software. Sometimes our systems themselves would have such vulnerabilities we had no idea about. Hackers are on the constant lookout to exploit them before developers can patch them up.

(Image Created on Bing.com)
SOCIAL ENGINEERING:
Not all cybercriminals use threat or urgency to scam you. The really smart one involves social engineering. Many have been cheated by someone they met online, got into a relationship of trust only for the person to ask for money and disappear. At times, people claim to be an old friend from college, reminding you of the good times you had. The facts match so you trust the person and again, after months of such correspondence – usually it is never a real meeting – they ask you for money to tide over an emergency, you trust and give, and then the person disappears, and you realise the friend this fraudster has been impersonating, has been dead years. The suave cybercriminals get a kick out of exploiting human emotions and trust, to manipulate victims into making mistakes or handing over information through clever storytelling, emotional appeals, or fake authority figures. But where did they get this information to cheat you: your social media accounts.
These are 25 of the most common ways in which you can be baited, hooked and caught in a web of digital scams where you can not only lose money but memories and peace of mind. But life need not be this difficult. There are some simple ways in which you can keep yourself and your family safe. Some you would have figured out by the very means in which the criminals try to cheat you. In the next part of this trilogy, we take a detailed look into how you can protect yourself with good digital hygiene, in a world awash with digital viruses and cybercriminals.
In case you missed:
- AI Taken for Granted: Has the World Reached the Point of AI Fatigue?
- And Then There Were None: The Case of Vanishing Mobile SD Card Slots
- Kodak Moment: How Apple, Amazon, Meta, Microsoft Missed the AI Boat, Playing Catch-Up
- One Year of No-camera Filmmaking: How AI Rewrote Rules of Cinema Forever
- Digital Siachen: How India’s Cyber Warriors Thwarted Pakistan’s 1.5 Million Cyber Onslaught
- Susan Wojcicki: The Screaming Legacy of The Quiet Architect of the Digital Age
- To Be or Not to Be Polite With AI? Answer: It’s Complicated (& Hilarious)
- What are Text-to-Video Models in AI and How They are Changing the World
- Rise of Generative AI in India: Trends & Opportunities
- The Great Data Famine: How AI Ate the Internet (And What’s Next)









