Felista Gor reflects on the major data breaches of 2023, what that portends for the future and what can be done to avoid them.
Companies frequently enter into agreements with their customers in which they pledge to spend money on offering them personalized services in exchange for them personally identifiable information. Customers rely on the company to secure their private information as they enter into this agreement.
However, with the worrisome rise in data breaches targeting both big and small businesses, it is inevitable for organizations to be vigilant. Companies are now more vulnerable than ever, and even major enterprises with the most advanced cybersecurity measures can be attacked. Small enterprises can draw lessons from the recent high-profile attacks and use them to create a security plan that will cover all bases.
Below we have compiled a list of significant data breaches that have taken place since January 1, 2023, their causes, impacts, and what you should do in the event of a breach.
What is a data breach?
A data breach constitutes sensitive, protected, or confidential data that is copied, communicated, viewed, stolen, altered, or used by someone not authorized to do so.
The incidents range from coordinated hacking attempts by individuals who take advantage of inadequately configured system security or carelessly discarded computer equipment or data storage media to steal identities, access accounts, and financial information, among other personally identifiable information.
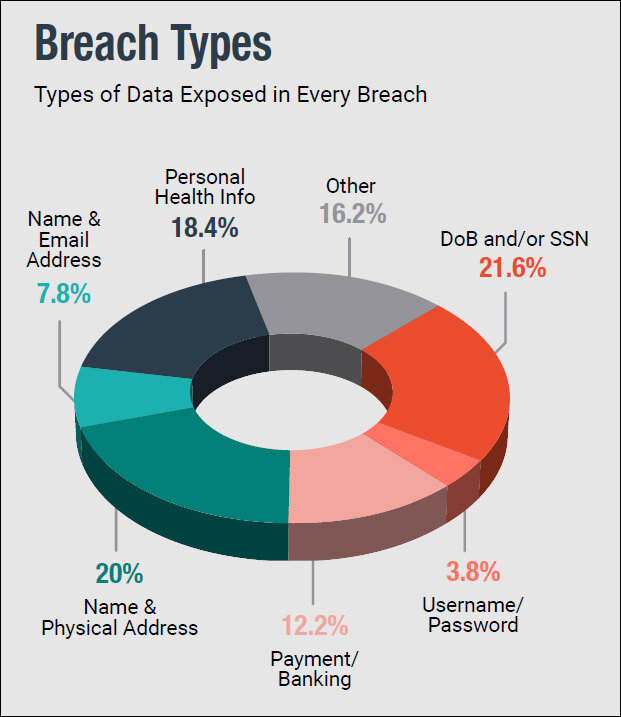
In the wrong hands, this information can inflict tangible losses on customers and businesses.
5 major data breaches in 2023
1. Google Fi: February 2023
Google Fi is a mobile virtual network operator service that provides calls, short message service, and mobile broadband using cellular networks and Wi-Fi and uses T-Mobile’s network for most of its connections. Google notified its customers using their Google Fi cell service of a possible data breach that resulted in personal data being stolen which was also believed to be in connection with the T-Mobile data breach that occurred earlier in January. According to Google, the data breach led to personal customer information, including phone numbers, SIM card serial numbers, account numbers, and mobile service plan data, being stolen.
Google says that hackers accessed limited customer information; however, hackers can use, for example, phone numbers to send phishing texts and trick customers into installing malware or use social engineering attacks to forcibly obtain other personal information.
2. JD Sports: January 2023
JD Sports, a high-street fashion retailer, suffered a data breach in which the attacker had access to the personal and financial information of 10 million customers. In an email to its customers, JD Sports confirmed that the security breach gave attackers access to data including email addresses, phone numbers, the final 4 digits of payment cards and or order details, full names, and billing addresses.
3. T-Mobile: January 2023
T-Mobile has been a victim of a data breach for quite some time. Recently, they discovered another breach that occurred in December 2022 but was discovered on January 5, 2023. During the breach, names, billing addresses, birth dates, account numbers, and other account data for 37 million customers were compromised.
4. MailChimp: January 2023
MailChimp’s data breach occurred barely six months after its previous breach. According to MailChimp, a threat actor gained access to its system tools used for customer support and account administration. The attacker conducted a social engineering attack on MailChimp accounts using compromised employee credentials. The threat actor accessed data attached to 133 MailChimp accounts.
5. Norton Life Lock: January 2023
The Norton Life Lock data breach occurred due to a credential stuffing attack, where previously breached customer credentials were used to break into accounts on accounts and sites that shared the same password, rather than a compromise of its systems. This data breach exposed personal information, including the first name, last name, phone number, saved passwords, and mailing addresses of thousands of Norton Life Lock customers.
What to do in the event of a data breach
The way things are going, the question is not if but when a data breach will happen. When a data breach occurs, you may become frantic as you try to diagnose the problem and communicate clearly with the people affected. These five pointers will ensure you do the right thing after a data breach.

a. Assess the situation
First, assess the data breach’s risk to customers. Risk assessment will inform you of the next steps, including whether to report the breach.
b. Be transparent
Do not try to cover up the data breach or hide details from those affected. When you hide details, customers will start to lose trust in your business on top of the negative news coverage. You must inform your customers promptly and advise them on the next steps to take.
c. Document everything
Every data breach should be documented and reported to the appropriate authorities. Record what happened, the steps you took, and why the breach was reported or not in some cases.
d. Learn from it
Once you identify the cause of the data breach, fix it. Shut down affected systems or resources to prevent others from getting affected as well and analyze what went wrong by investigating your business’s security mechanisms and the inefficiencies of the security solutions. Additionally, ensure necessary preventive measures like staff training are implemented to prevent future incidences.
e. Make sure you notify everyone affected
Release an official notification with the help of your PR team to inform the related businesses, employees, and customers about the incident. This helps limit the breach’s impact.
Final Thoughts
A data breach of any magnitude erodes the trust of customers, which is hard to recover. It is imminent that businesses learn from the incidents that have already occurred and develop strategies that will help them prevent or, in the case of a data breach, get back on their feet sooner rather than later.
In case you missed:
- None Found










5 Comments
Well put Felista, this is an informative piece.
This guide is so complete. I love how detailed it is, shedding light of the jargons and ensuring that novice readers get a hang of everything.
My favorite lines:
The sooner you understand that your business is at risk of cyber attacks, the more vigilant you’ll be. It’s no longer asking about if an attack happens but about when it happens and how to recuperate from it.
Businesses need to keep their clients informed when a cyber attack happens.
Very informative . Many Thanks Felista
This is quite educative, especially IT related, for many who have no knowledge on this.
Such great insights. Nice work Felista