Hacking, till now, has been about money but for the first time a ransomware group demanded money to not overthrow an elected government of a nation, finds out Satyen K. Bordoloi

Something unprecedented happened in the month of May 2022. The Conti Ransomware hacking group threatened to overthrow the newly democratically elected government of Costa Rica if they aren’t paid 20 million dollars. Perhaps it was to be expected: research has shown that the group is based out of Russia.
On May 8, Rodrigo Chaves became President of Costa Rica, along with 57 other Congressmen, who were part of the newly elected Legislative assembly. He got a four-year term to rule the highly stable and rich Latin American nation. The Conti Ransomware attack had begun in April, with hackers managing to infiltrate 27 government institutions including municipalities and state-run utilities. Initially, the Conti group demanded $10 million but increased it to $20 million in May.
What is unprecedented is that they have threatened to overthrow the government if they are not paid that money and even posted an appeal online to Costa Ricans to “go out on the street and demand payment”. It is as if the group looks at themselves as revolutionaries.
In a ransomware attack, hackers gain access to computing systems through malicious code implanted into the devices using various methods. They then proceed to lock up the system. A user can get access back to a locked system only when they pay the ransom demanded. The ‘ransom’ is the reason this type of hacking software is called ransomware.

A few years ago, ransomware was not the main hacking method for cybercriminals. Even when used, the demand for payment to free the systems were small sums of money. In the last few years though, attackers have become increasingly bold.
In May 2021, Colonial Pipeline – an American oil pipeline system carrying oil mainly to the South-Eastern United States, was hit with the DarkSide ransomware that impacted computerized equipment managing the pipeline. The company had to shut down all pipeline operations to contain the attack affecting 45% of US’ East Coast fuel supply. Panic buying shot up fuel prices leading President Joe Biden to declare a state of emergency on May 9. The company had to pay $4.4 million worth of Bitcoins to get back control of their systems. This took around a week.
The new Costa Rican president Rodrigo Chaves, has also had no option but to declare a state of emergency. On May 16 he held a press conference where he said, “We are signing this decree, precisely, to declare a state of national emergency across the entire public sector of the Costa Rican state, and allow our society to respond to those attacks as criminal actions.”
This measure gives the government sweeping powers to bypass the legislative assembly and take its own decisions e.g., to allocate public funds without legislative consent. The president isn’t wrong to have such a reaction.
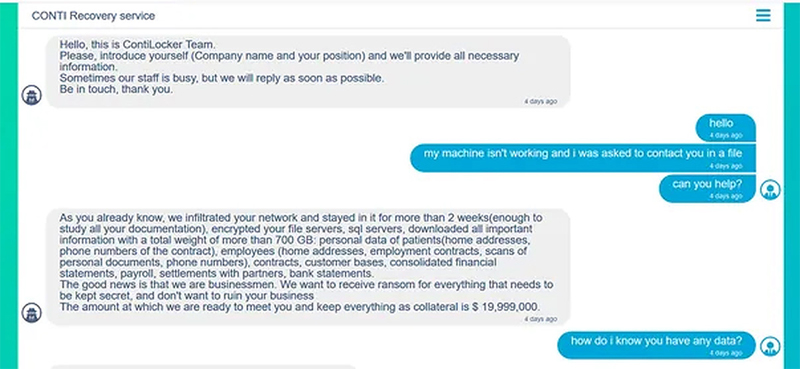
The Conti hacking group posted over 600 gigabytes of government data online with the threat to publish more. Not just that, on their darknet website the group threatened to delete the decryption keys needed to take back the attack and restore the systems writing, “There is less than a week left when we destroy your keys, we are also working on gaining access to your other systems, you have no other options but to pay us.”
Despite the threats, Chaves has given no indication that he intends to pay the ransom. He has blamed his predecessor Carlos Alvarado for not securing the nation’s cyber infrastructure. Brett Callow, a ransomware analyst at Emsisoft, told USA Today, “We haven’t seen anything even close to this before, and it’s quite a unique situation.”
However, Callow does not believe that their main intention is to overthrow the government, stating, “The threat to overthrow the government is simply them making noise and not to be taken too seriously, I wouldn’t say. However, the threat that they could cause more disruption than they already have is potentially real.”
The US Department of State has taken this threat seriously. On May 6, they announced that they were offering up to $10 million, “for information leading to the identification and/or location of any individual(s) who hold a key leadership position in the Conti ransomware variant transnational organized crime group” and $5 million “for information leading to the arrest and/or conviction of any individual in any country conspiring to participate in or attempting to participate in a Conti variant ransomware incident.”
The State Department has reasons to go after this group as they had previously targeted US healthcare services, threatening to go after any opponents of Russia during the current war in Ukraine. Though it is not clear that the hackers are affiliated with any government, but leaked chats show that they support Russia.
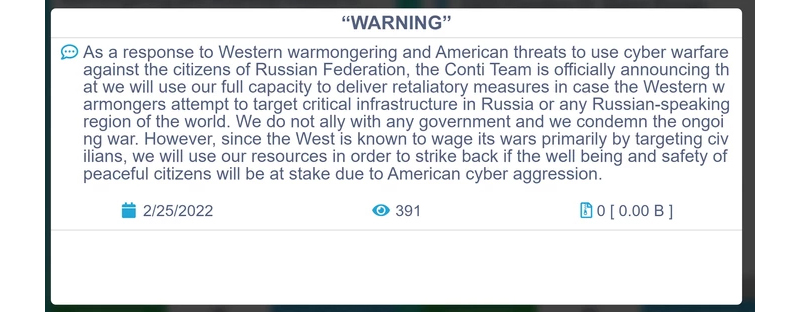
That is another bizarre twist to the tale. The Conti gang is not just being pursued by the law, but also by one or some of their own with an insider leaking a massive cache of internal chats after their leaders showed themselves to be aggressively pro-Russian at the beginning of the Ukraine war stating that they will use, “all possible resources to strike back at the critical [infrastructure] of an enemy” that launches a “cyberattack or any war activities against Russia”.
All this pressure has borne results. Though on one side smaller nations are fearing that they’ll be next to be attacked like Costa Rica was, news is coming out that the cybercrime group has officially taken down its attack infrastructure. This does not mean they have shut shop but only that it’s split into smaller groups and does not signal an end of Conti groups activities. It could be quite the opposite.
This attack on Costa Rica, the rhetoric used, and the tacit support of Russia means we have entered a new era of cyber warfare where the lure of money will tie in with the lure of power rouge state actors like Russia have. Alongside wars, it is groups like Conti Ransomware gang and hackers who will pose an equal threat to the stability of the world. And unless nations unite against them, the damage won’t be any less than actual wars.
In case you missed:
- Digital Siachen: Why India’s War With Pakistan Could Begin on Your Smartphone
- Digital Siachen: How India’s Cyber Warriors Thwarted Pakistan’s 1.5 Million Cyber Onslaught
- Zero Clicks. Maximum Theft: The AI Nightmare Stealing Your Future
- AI’s Top-Secret Mission: Solving Humanity’s Biggest Problems While We Argue About Apocalypse
- Is Cloud Computing Headed for Rough Weather
- India’s Upcoming Storm of AI Nudes & Inspiring Story Of A Teen Warrior
- Why Elon Musk is Jealous of India’s UPI (And Why It’s Terrifyingly Fragile)
- Yes, an AI did Attempt Blackmail, But It Also Turned Poet & erm.. Spiritual
- Copy Of A Copy: Content Generated By AI, Threat To AI Itself
- Microsoft’s Quantum Chip Majorana 1: Marketing Hype or Leap Forward?










1 Comment
Thank you for sharing the information about the hackers vs state dawn of ransomware, it is good article , keep sharing.