For individuals and enterprises, protecting their digital soul should take precedence over discovering the hidden treasures of ‘data’, states Sairaj Iyer.
In 2023, forged documents would score last in the context of frauds.
Forging documents has become painstakingly boring in recent years if statistics are to be believed. You may want to watch the recently released thriller Farzi (Shahid Kapoor on Netflix) or Money Heist (Netflix) for some cinematic imagination. In reality, forging currency notes has few takers in the unorganized world. Besides, there is little left in the category of forging except passports, land-records, or cheque-sleeves.
Online photo-editing tools and availability of a high-mega-pixel camera have made it easier to copy-paste and forge documents. Besides, two-factor authentication and computer-analytics have resulted in the death of what was once known as an art. Think of it, what value does a forged cheque really offer? By the time this manipulated cheque gets presented at a bank or an ATM processing center, it will get caught in a matter of a few seconds. Forging a cheque could land a two-year jail term in addition to a fine. Last year only a dozen cases were reported in the Indian media.

For professional forgers, there are plenty of opportunities. These include scamming credit cards, bank accounts, websites, malware, and anything related to your profile, your social identity, or the identity of the businesses you are associated with.
Think about it, to the new age hacker, entering somebody’s smartphone is far more lucrative than forging somebody’s insurance or a cheque. Forging insurance may appear lucrative, but it could be a horrendous approach given the amount of analytics in play. Spoofing a smartphone seems easy and would open a host of opportunities – there’s certainly banking apps; a wallet-app such as PayTm or PhonePe; the Gmail which can be harvested; then there’s social profiles like Facebook or Twitter; and then there’s private photos which too can be harvested resulting in unimaginable agony for the smartphone owner.
And the best part… Unlike physically sniping at an unsuspecting victim’s wallet, professional hackers can be located ten-thousand miles away and intrude your smartphone through a file shared on WhatsApp or through a code injected via a website or even free Wi-Fi. They could also socially monitor your activities online and attempt hard attempts at it. And it is not always that they are going to gain access to your banking account and make money. Many a times, your private information is sufficient to earn money. Knowing the password of your Gmail or iOS account may open significant avenues – saved passwords, login credentials of businesses you are associated with, scanned copies of educational records, PAN card details, Aadhar card etc. In other words, your identity that you have underrated is revenue of sorts for scammers.
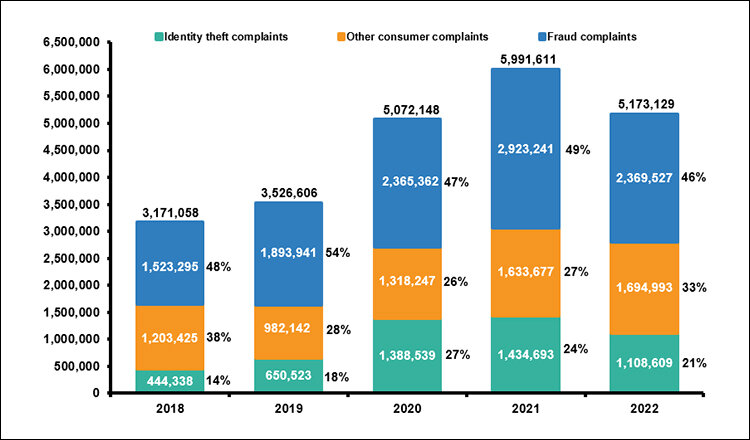
(Source: US-Federal Trade Commission, Consumer Sentinel Network)
Identity Access Management
The term identity access management (IAM) has gained significant traction in recent days. From an enterprise standpoint this involves a series of governance strategies and a well-defined guideline of workflow. From a non-enterprise or personal standpoint, Google’s Auth0 is the perfect example of how a private entity manages your identity. AWS has an IAM engine, and every cloud provider out there has some form of IAM protocol. These IAM protocols govern how to save your passwords, auto-fill forms, user behavior across mobile and desktop, cookie related information, and in some cases your entire browser history that says a lot about you.
The term Identity Access management has come a long way from the era of Active Directory management which was first announced in the 1990s to authenticate users on the Windows OS. Like a white page, the directory has the listing details of users, applications, permissions, domains, security services, and access permissions. Microsoft Teams and Outlook both utilize these principles of AD. To understand this better, here are two examples – employees no longer a part of the official network cannot access their official email and even computer. Similarly, an employee on a network could start any computer using their login credentials and find the exact Desktop.

Identity in the Online World
The proliferation of digital services and internet has resulted in a massive influx of new users. The rise in number of users may have been one reason for even the decentralized world to consider something as revolutionary as ‘Soul-bound tokens.’ Cryptocurrency or decentralized technologies are usually anonymous except for their unique network values and hash keys. Hence, a whitepaper titled soul-bound tokens may have left even the blockchain-purists bemused.
Ethereum co-founder Vitalik Buterin, Puja Ohhlaver, and Glen Weyl in a whitepaper dated May 2022 argue the need for Soul-Bound tokens given the emphasis on identity and credentials. The authors explain that there is a compelling need for proving identity given the flourish of Web 3.0. The whitepaper pitches for the need to have non-transferrable and non-tradable NFTs (non-fungible tokens) to validate authenticity of credentials. Unlike traditional crypto operations, this would be proof of origin and not involve a staking mechanism but rather be issued by an entity. Even the most ardent critics of crypto may find the whitepaper tilting in favor of opening up identity. This hence could result in a more open blockchain where users are easily identifiable. Wait, IAM tools are not important just because the blockchain world has released a whitepaper, here are some use-cases.

Use-Cases
Existing IAM tools and solutions enable IT administrators to enable user management via role-based controls, access to data, ability to form groups, password policies, and even multi-factor authentication tools. Some advanced services also offer a remote wipe service nestled as part of a mobile device management (MDM) module.
The whitepaper on SBTs on the other hand imagines advanced use-cases and features. SBTs could be utilized as publicly verifiable records which could be handy in the event of job vacancies, or in the gaming industry to earn badges. SBTs could also be handy in credit bureaus, government offices, and even Universities since these entities have traditionally relied on paper for documentation. It may be easier for a forger to duplicate a certificate printed on a sheet, but it would be next to impossible to counterfeit a document with a unique hash value. We could make it impregnable by adding a multi-factor authentication to the document.
As such, the HR function invests significant resources in verification processes prior to onboarding prospective employees. Educational and work-experience certificates in the form of SBTs would not only streamline the HR process but also reduce the cost of hiring activities. In simpler words, SBTs are like the SSL (Secure Socket Layer) certificate issued to a website. You may argue that SSLs can be bought and sold. Well, that is true but in the blockchain world, SBT is a cryptographic key which could only be created once. And it cannot be sold or purchased the way one trades NFTs or Bitcoins.
Are IAM Tools Impregnable? Yes, but not Really!
When it comes to IAM, the common advisory is to adopt a zero-trust principle. In addition to partnering with vendors demonstrating a strong track record in security and compliance, solutions are expected to follow industry standards such as ISO 27001, SOC-2, and PCI DSS. Despite robust implementation standards, IAM solutions have failed in the recent past.
Recently, hackers gained access to the IAM system of SolarWinds, an IT management software company and obtained privileged access to customer networks. The Capital One Data breach, a 2016 data breach reported at US-hotel chain Marriott involved significant loss of customer data. Then there is the data breach at credit reporting agency Equifax in 2017 where millions of profiles and their credit data were lost online. These examples signify the need for sound implementation standards.
Identity is not only a technical concept but has a profound economic theory as well. According to a Princeton University paper, identity economics captures the idea that the personal identity of an individual – an economic agent – is important for explaining individual economic behavior. The paper also adds that personal identity influences people’s decisions, including their economic decisions. As a business or individual, your identity is constantly on the expose. To a business, the risk is higher given there are multiple avenues to harvest data. For example, try searching for your bank on Twitter. You will find at least a dozen odd imposters.
From a personal use-case, there have been countless tales of Facebook users who have complained that messages were sent from their account to their friends seeking money. Stealing identity is a crime that cannot be thwarted by an anti-virus or a malware protector alone but demands common-sense. Fortunately, leading an offline life is a serendipitous choice for individuals but is suicidal for the enterprise where digital is bread and butter.
Thousand tech-marketers will sing peans and jingles like ‘Data is oil, so let’s drill down, let’s mine and refine… “
Well, yes, data is important, but Identity is the soul, the fabric of life, freedom, and our place in the light.’
In case you missed:
- None Found