Dhananjay Ganjoo, the India Managing Director at F5 Inc in a conversation with Sairaj Iyer answers how technologies such as distributed API protection and the Zero Trust approach are helping build a secure enterprise
Customers need not see safety as a major reason of associating with a brand until they turn victims. This lack of vision by a customer should not be reason for enterprise complacency in tackling aspects of Cybersecurity which has become an intensely discussed enterprise topic in a post Covid era.
The threat-matrix has evolved. For instance, India now ranks second only to the US in most security threats on cloud, followed by Australia, Canada and Brazil (according to a McCafe Enterprise Advanced Threat Research Report). ISACA (Information Systems Audit and Control Association), in its latest threat landscape finds 33 percent respondents (mostly CISOs, Security heads and Auditors) experiencing more cyberattacks than the last year. The major concerns in this year’s survey findings were Cyberattacks, organizational reputation, data breach concerns, supply-chain and business disruptions.
Besides the usual risks, there’s a double-digit spurt in APTs, Ransomware, DDoS, Injection flaws, and even sensitive data exposure and leakages. The only thing that changes this year is the confidence among respondents to tackle such cyber-attacks — 77 percent of them. Sadly, the thin line between confidence and over-confidence is narrower than make or break situation enterprises often find themselves in. The spurt in the aggregation business, customers over-reliance in apps/internet, and the spurt in data breaches are all reasons that can make or break an organization.
Dhananjay Ganjoo, the India Managing Director at F5 Inc answers questions on how technologies such as distributed API protection and the Zero Trust could help the enterprise. For the unaware, F5 Networks is the parent of leading technologies such as Nginx, Shape and Volterra. Besides explaining the contemporary threat matrix, Ganjoo also reveals proactive strategies of securing a no-code environment.
Sairaj Iyer: What is the threat matrix that CIO/CTOs are looking at in 2022?
Dhananjay Ganjoo: The variety of flexible, cost-effective consumption options has increasingly led organizations to opt for multi-cloud environments in recent years. It has caused the threat matrix to evolve dramatically and has significantly expanded the attack surface, making them vulnerable to cyber threats. Today, businesses need to protect their data from various attacks, such as malware, enhanced SQL injection, DDoS attacks, file inclusion, cross-site scripting, man-in-the-middle attacks, botnet attacks, and path traversal. With the growth in the mutation of threat vectors, businesses need to assess and intercept the attacks to protect their web applications. The need of the hour is for businesses to build end-to-end network security, which will help them protect their network, data, and ultimately their customers, via security solutions that rapidly detect and neutralize security threats.
SI: The next-gen Fintechs, the likes of Blockchain, IoT and aggregators boast of customer interactions in seconds. How different is their threat matrix from a traditional enterprise?
DG: Any business in the fintech space deals with its users’ personal and sensitive data, which is an attractive target for bad actors. They also rely on several APIs to provide the end-user with a seamless digital experience for their financial needs. Using botnets and stolen credentials, attackers try to exploit the vulnerabilities which cause substantial data breaches and costly losses and expand the threat matrix to API gateway and API management.
SI: Is User Digital Experience also a challenge that CISOs often have to tackle?
DG: Customers now demand better experiences from businesses in the digital and real world. They are aware of their choices and do not hesitate to exercise that power. This leaves businesses with no choice, but to be constantly agile by reducing their response time to market opportunities, to remain competitive. They additionally might deploy applications by opting for environments best suited for their business, for a superior user digital experience. This often leads to several challenges such as managing a complex app portfolio, a lack of end-to-end visibility, and infrastructure lock-in, limiting the ability to move an application. These challenges lead to damaged customer relationships and diminished business success.
SI: What does Distributed API protection do?
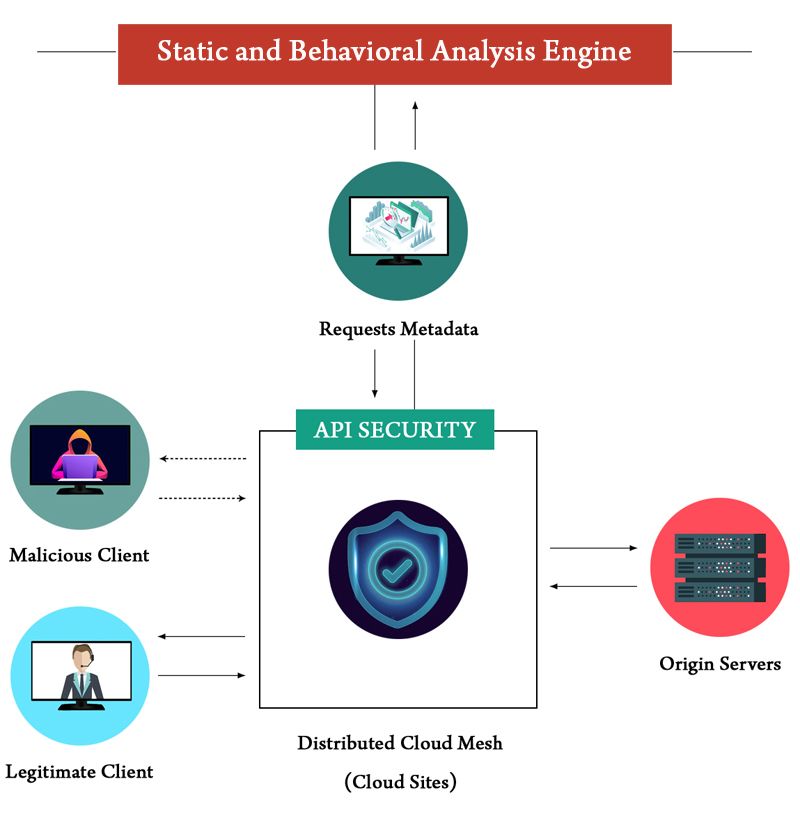
DG: Modern applications depend on APIs to deliver a positive digital experience for the customers. However, this makes it difficult for businesses to distinguish a legitimate user from a malicious user as security teams struggle to manage and identify exponential number of endpoints and connections across their infrastructure. Additionally, sensitive data is often unintentionally exposed and may cause costly data leakage. F5 Distributed API protection is a SaaS-based platform that automatically discovers API endpoints connected to applications via allow-list and monitors irregular behaviour. It uses AI/ML to provide discovery and deep insights in real-time and eliminate vulnerabilities at the source.

Dhananjay Ganjoo, Managing Director, SAARC, F5 Networks
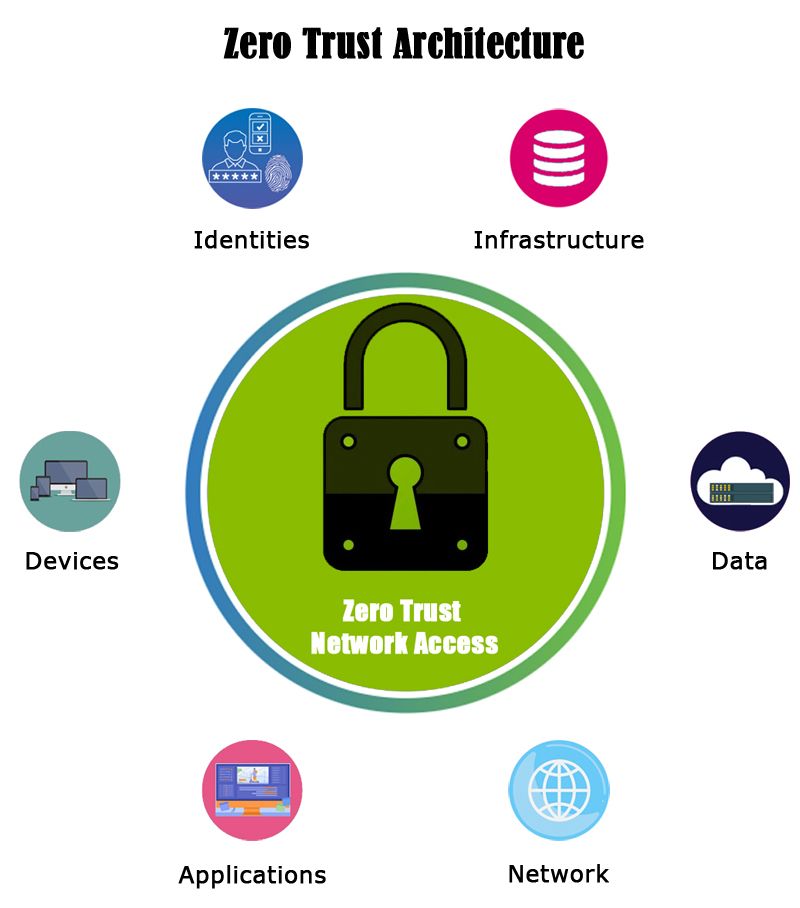
SI: Do CIOs trust the Zero Trust approach? Many CISOs have elaborated on it. Do you look at it as a marketing fad or is it a real boardroom discussion?
DG: Zero Trust architecture is a security model built on the core principle of verifying every user and device-both inside and outside an organization’s perimeters-before granting access. It is more relevant and vital today than ever, mainly when businesses have shifted to a hybrid workforce. Users are connecting from various locations and devices to access applications. Hence, businesses must include a ‘Never trust, always verify, continuously monitor’ approach to protect the app from bad actors and ensure only the right people- and only those people-have access to the suitable applications or information at the right time. Customizing the architecture as per the zero-trust model can help increase efficiencies in business processes and enhance user productivity. This approach undoubtedly needs to be of a priority agenda for board room discussions.
SI: Speaking of the hybrid workplace model, don’t you think there is a redundancy risk? For instance, MDM too became irrelevant in the post-Jio era (Connecting to an office LAN for internet seems so passive)?
DG: A robust network security system is a must for the BFSI sector, irrespective of their employees working over the LAN, wired, wireless, or internet connections to protect the workstations from sensitive financial data thefts. The pandemic-induced hybrid model demanded that banks and financial institutes modernize their operational processes and business systems to provide an uninterrupted banking experience to the customers. The tailwind from the newer security deployments will continue to make the network security stronger with added capabilities to manage access better, detect irregular behaviour, and secure applications irrespective of its deployments.
SI: How complicated/challenging is the F5’s Cloud web app and API protection for implementation?
DG: Traditional web application firewall (WAF) requires the security teams to follow a comprehensive list of steps for deployment and blocking. Each deployment layer needs a different skill set, with an additional layer added to the WAF. F5 Web Application and API Protection (WAAP) is a SaaS-based web application firewall (WAF) with bot protection and advanced API security. The entire process is intuitive with simple UI, making implementation and deployment easy and seamless. The comprehensive list of steps to onboard any application can be covered within 5 minutes, dramatically simplifying operations with consistent security policies across the entire deployment. In addition to this, F5 Distributed Cloud WAAP includes DNS security and DDoS protection, all as an integrated add-on on the platform, quick and straightforward to implement and deploy.
SI: Businesses these days are making plans of moving to no-code environments even as F5 made strong inroads into meatier operating systems such as Nginx, Shape, and Volterra. Is there a no-code stack that you are currently planning to build or deploy for your customers?
DG: In recent years we have seen low-code/ no-code platforms rise to popularity and mainstream adoption by businesses to develop applications. According to Gartner, over 75% of large enterprises will use low-code development tools by 2024, and over 65% of all application development carried out using low-code tools and methods. With this growth, businesses are also increasingly facing security and reliability challenges. These low-code/no-code platforms provide limited visibility and control of the application codes making their critical business processes and data highly vulnerable. F5 and its acquisitions of NGINX, Shape, and Volterra (products from Shape and Volterra are now converged under F5 Distributed Cloud Services), help deliver superior value to customers by providing end-to-end application security solutions with inbuilt sophisticated AI, cloud-based analytics, and anti-fraud technologies. Additionally, they protect every aspect of the ‘code to customer’ journey against losses from online fraud, reputational damage, and disruptions to critical online services. Our adaptive suite of applications ensures that we are well equipped to cater to the applications built using no-code platforms.
In case you missed:
- None Found










1 Comment
Thank you for sharing the information about 2022 threat matrix is zero trust approach and distributed api technology relevant, it is good article , keep sharing.