Chinese researchers claim to have figured out an algorithm that can use existing quantum computers to decrypt classical encryption heralding the age of quantum hacking writes Satyen K. Bordoloi. Is anything digital safe anymore?
Your debit card pin has four numbers. There are ten thousand combinations any four numbers can make. Any system that wanted to crack your pin would take a decent amount of time to figure it out. But using quantum methods, this can be done exponentially faster.
That is because in 2019 Google researchers calculated that its quantum computer was 158 million times faster than a supercomputer. And this is despite quantum computing being in its infancy. Thus if quantum computing were to be used to break cryptographic codes that form the basis of most digital security systems, they would be extremely fast.
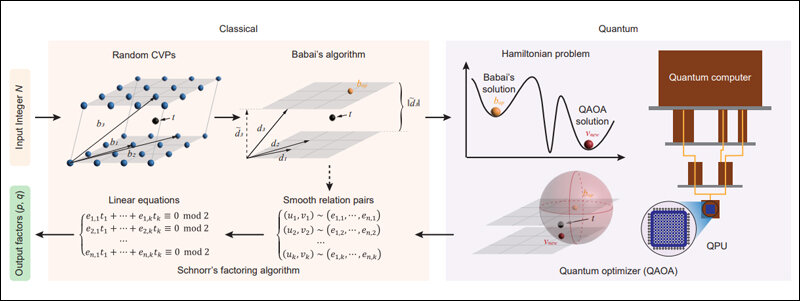
If this research paper published by Chinese researchers on 23rd December is to be believed, they have done just that. Researchers from different universities in Beijing and Zhengzhou, China, developed an algorithm that can break the RSA-2048-bit encryption key, the most commonly used form of online encryption, using quantum bits.
Quantum Hacking
This is significant for two reasons. One is because RSA algorithms are thought of as un-hackable from a practical point of view e.g. RSA-2048 encryption would take classical computers 300 trillion years to crack. Secondly, Quantum hacking was thought to be years, if not decades, away.
What this latest research paper shows is that Q-Day is closer than anticipated. Q-day is the day quantum computers will be able to use superposition and quantum entanglement of multi-state qubits to factor in large prime numbers that make up our public encryption systems, thus breaking the encryption algorithms widely used across the world.
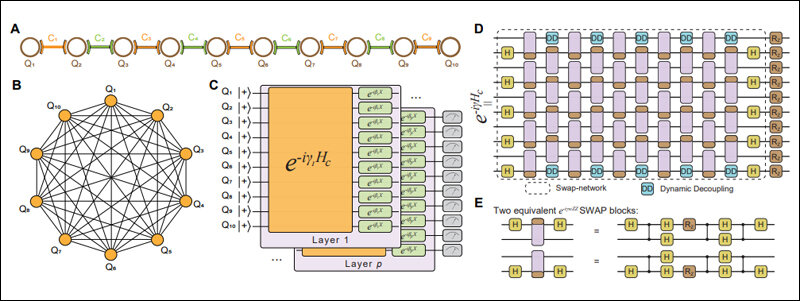
What this paper claims, is that a “quantum circuit with 372 physical qubits and a depth of thousands is necessary to challenge RSA-2048 using our algorithm.” This has alarmed computer security experts because IBM already has their quantum computers on the cloud for people to test. IBM now plans to unveil their new 433 qubit Osprey system in the next few months and make it available for customers.
Rhythm of Algorithm
(Image Credit: Arxiv)
Shor’s algorithm, developed in 1994 by Peter Shor, is an algorithm for a quantum computer to find the prime factors of an integer. If a quantum computer with enough qubits can refrain from succumbing to quantum noise and other quantum-decoherence phenomena, then Shor’s algorithm could be used to break public encryption; not just the RSA scheme but also Finite Filed Diffie-Hellman key exchange and the Elliptic Curve Diffie Hellman key exchange.
If the Chinese researchers are correct, this heralds a significant moment in the computing history of the world because this means no digital system, no matter how strong its encryption, is free from quantum hacking. Security experts had already expected this to happen in a few years as quantum computing became better, but to have it figured out already, has shocked many.
However, not all hope is lost. Peter Shor, the MIT scientist whose equation is the basis of most digital security systems talked about the development to Financial Times and said that he didn’t think the research paper was wrong. However, he points out that the Chinese researchers had “failed to address how fast the algorithm will run,” which means that it could still take millions of years – if not trillions – to crack RSA-2048.
Breaking the Code
This is not the first time that a theoretical and mathematical way to factor RSA algorithms has been shown. In 2019 scientists at Google and Royal Institute of Technology in Stockholm showed in a paper they had written, how to factor 2048-bit RSA integers in 8 hours with 20 million noisy qubits.
Despite this, the main thing to consider is that what the Chinese researchers have highlighted is only a theoretical way of breaking the RSA code. However, since the number of qubits in a system they claim to need to break the RSA encryption already exists, perhaps their hypothesis – if everything else pans out to be good – could be tested with existing quantum computers.
Safety first

Does that mean nothing is safe? Not really. The solution to quantum hacking, interestingly, also lies in the same domain: quantum cryptography. This is a method to use naturally occurring properties of quantum physics to secure and send data in a way that only the person with the right key can open it. This is practically unhackable because altering one of the entangled particles would alter the other as well.
However, the capability to do that in practice is still some time away. Hence, papers like this one by Chinese researchers give the required push to developers worldwide to expedite research so that quantum cryptography is ready before quantum hacking is.
In case you missed:
- Google’s Willow Quantum Chip: Separating Reality from Hype
- Microsoft’s Quantum Chip Majorana 1: Marketing Hype or Leap Forward?
- Why a Quantum Internet Test Under New York Threatens to Change the World
- Quantum Internet Is Closer Than You Think, & It’s Using the Same Cables as Netflix
- Prizes for Research Using AI: Blasphemy or Nobel Academy’s Genius
- AI Taken for Granted: Has the World Reached the Point of AI Fatigue?
- The Great Data Famine: How AI Ate the Internet (And What’s Next)
- AI Hallucinations Are a Lie; Here’s What Really Happens Inside ChatGPT
- To Be or Not to Be Polite With AI? Answer: It’s Complicated (& Hilarious)
- You’ll Never Guess What’s Inside NVIDIA’s Latest AI Breakthrough











1 Comment
I always thought that encryption tied to a fixed number of bits 128, 256, 4096, etc. (constrained) would eventually be cracked.
We need to move to an unconstrained form of encoding that makes it much harder or essentially impossible to crack.
You can do this with image files using features offered by a program called imscram.