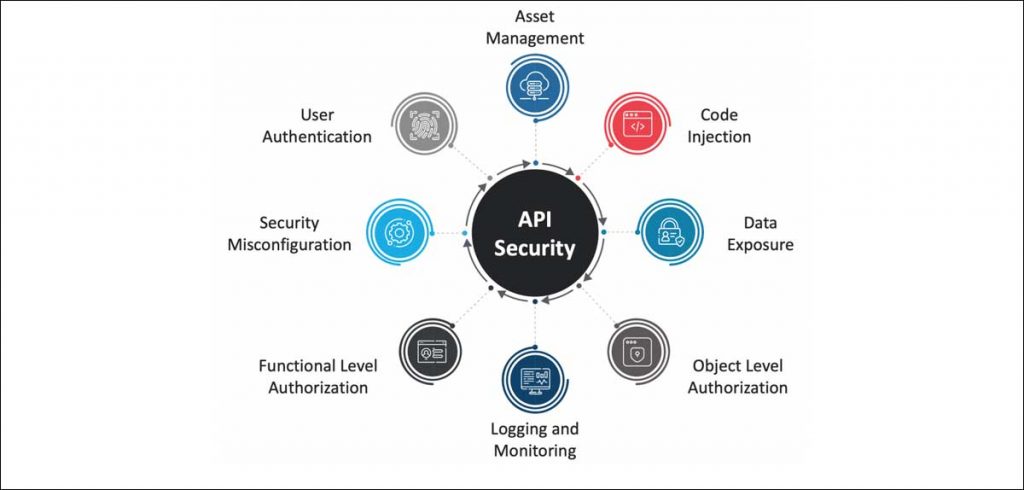
Out of a total of 16.7 billion malicious requests that target APIs, roughly 30 percent target shadow APIs..
APIs are little bits of code that allow software programs to communicate with other programs, for more information on this you can check out our previous post titled A beginner’s guide to APIs. Shadow (or Rogue) APIs, on the other hand, are APIs that are running within organizations, but without the approval of the IT or security teams. While the intentions behind these APIs could well be harmless as they are often used for their testing abilities or even as a workaround, the attacks that an unsecured API opens you up to can cause serious harm. Out of a total of 16.7 billion malicious requests that target APIs, roughly 30 percent target shadow APIs. These include APIs that are unknown, unmanaged, and unprotected.

Malicious API traffic
Named after the shadow IT problem which refers to the practice of deploying unsanctioned software to bypass limitations and restrictions set by IT teams, some call Shadow APIs the DevOps version of this problem. Since APIs are so modular, powerful, and easy to use, the lure of deploying one now and worrying about security later, is great, to say the least. That being said, however, here are a few examples of why you shouldn’t deploy an unsanctioned API as a quick workaround for any sort of issue. The first example would be the infamous Twitter breach at the beginning of 2022 which Twitter revealed was caused by an API vulnerability. 5.4 million users had their data compromised while the hacker allegedly sold 400 million Twitter profiles on the dark web.
Other examples include Optus, Australia’s third-largest telecommunications company, where a publicly exposed API endpoint that didn’t require authentication caused 11.3 million customer records to be leaked with an estimated financial impact of over $140 million. Yet another example is the cryptocurrency platform 3Comma, where hackers gained access to a stockpile of API keys which allowed them to get away with about $22 million in cryptocurrency. And the hits keep coming, as API traffic accounted for about 71% of total net traffic last year, the attack surface has grown immensely and is growing harder to secure by the minute. With organizations averaging about 600 APIs and over a billion API calls, malicious API traffic is also seeing an astronomical rise with 2021 records showing a 681% growth in one year.

The Cure for Zombies
Now unlike Rogue or Shadow APIs which are APIs deployed without the knowledge or sanction of relevant IT teams, Zombie APIs are APIs that used to be sanctioned but have since been forgotten and are not being maintained and monitored anymore. There are a number of ways that Zombie APIs can be exploited including using them to carry out the notorious DDoS attacks that enterprise organizations have grown to know and fear. The interesting thing about API security is that while malicious API traffic may not be avoidable, leaving endpoints insecure is, with due diligence and the right tools. You want to avoid API sprawl at all costs, which is a situation in which your APIs are all over the place and you can’t even remember what half of them are for.
API discovery and governance should be step two, as you want to keep visibility at a maximum and that attack surface as small as possible. This means keeping a detailed inventory of all APIs in use and decommissioning unwanted APIs on a regular basis. This also includes tracking, monitoring, and logging API use as well as fixing vulnerabilities. Using API proxies to monitor all outgoing API requests is a good way to look for suspicious behavior among APIs. Frequent automated API audits as well as strict adherence to compliance all add to the overall protection against malicious API traffic. For those who are willing, there are a number of tools available that do most of this for you, like Threatx which automatically detects Shadow and Zombie APIs.

DevSecOps
Another tool for API security is Reblaze, which is a cloud-based security platform that features real-time API monitoring. Postman is an API security tool that allows you to send auth details with your API requests, adding another layer of authentication and security. Additionally, you can use Google’s Apigee Sense to detect suspicious API behavior, or APIsec if you believe in DevSecOps, which you should. In conclusion, this year we have already had a number of major data breaches including one at The Bank of America, and another at the popular project management platform Trello. With organizations focused on production and more interested in spinning up new APIs and less interested in securing and maintaining the old ones, the problem of Shadow and Zombie APIs is only going to get worse, unless we make security a priority.
In case you missed:
- Mainstream AI workloads too resource-hungry? Try Hala Point, Intel’s largest Neuromorphic computer
- South Korean firm develops drone that flies on hydrogen fuel
- CDs are making a comeback, on a petabyte-scale capacity!
- How AI Is Helping Restore the World’s Coral Reefs
- Humans Just Achieved Teleportation? Clickbait vs. Facts
- Pi Coin vs Bitcoin: Round 2, Mainnet Launch
- A Glowing Plant Could Be Your New Night Lamp for $29
- California startup develops app to sell sunshine at night
- NVIDIA’s Isaac GR00T N1: From Lab Prototype to Real-World Robot Brain
- From Fridge to Fusion Reactor, How Mayonnaise is Facilitating Nuclear Fusion